
CyberRisk Control CISO 360
A crucial observation of cybersecurity to ensure the overall health and integrity of your organization.

A crucial observation of cybersecurity to ensure the overall health and integrity of your organization.
Healthy cybersecurity is essential to protect sensitive corporate information and assets from cyber threats such as hacking, phishing and malware attacks. These threats can result in financial losses, reputational damage and loss of customer confidence. In addition, as cyber threats become increasingly sophisticated, regulatory compliance and legal liability issues may also arise (for example, Privacy Act 25). Understanding cybersecurity can help leaders make informed decisions to protect their business and mitigate potential risks.
A cybersecurity audit is an independent assessment of a company’s cybersecurity practices, policies and systems. The objective of the audit is to identify vulnerabilities, risks or areas for improvement in the company’s cybersecurity posture. It can be the first step towards achieving certification such as NIST, CMMC, ISO27001 or SOC.
According to NIST, a cybersecurity program is divided into five main functions. These five functions complement each other to help organizations effectively manage cybersecurity risks and improve their overall cybersecurity posture over time.
This feature helps organizations identify and understand their cybersecurity risks by identifying assets, systems and networks that need protection, as well as potential threats and vulnerabilities that could compromise them.
This function helps organizations protect their assets, systems, and networks from cybersecurity threats by implementing appropriate security controls and technologies.
This function helps organizations detect and respond to cybersecurity incidents by implementing appropriate detection and monitoring systems, as well as incident response plans.
This function helps organizations respond to cybersecurity incidents effectively and efficiently. This includes containing the incident, mitigating its impact, and taking steps to recover from the incident.
This feature helps organizations recover from cyber security incidents by implementing disaster recovery and business continuity plans, and taking steps to return to normal operations as quickly as possible.
Our CISO-360 Cyber Risk Control audit tool is specifically adapted to be malleable according to the size, human and financial capacity of your organization. It is structured in 3 groups of controls according to the CIS standard.
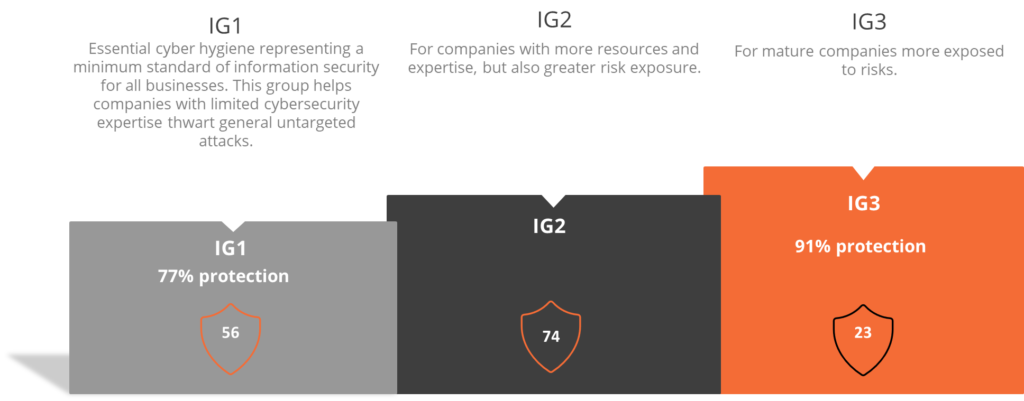
The CISO-360 CyberRisk Control tool provides a report detailing the audit findings on 18 cybersecurity topics and recommendations for addressing identified vulnerabilities or risks. The tool also provides management indicators that can then be monitored.
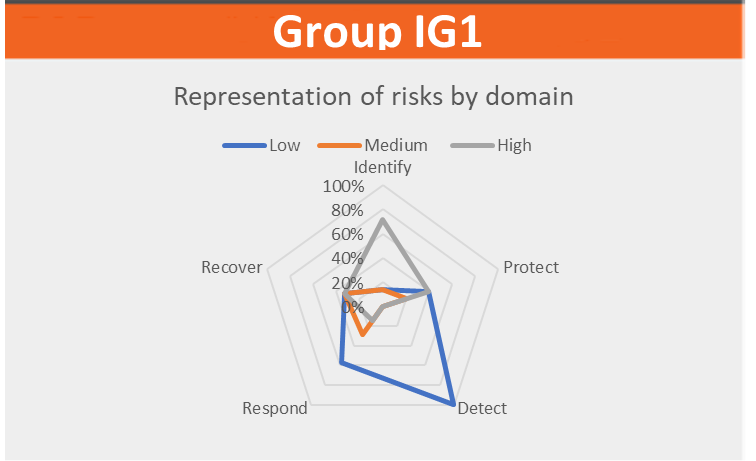
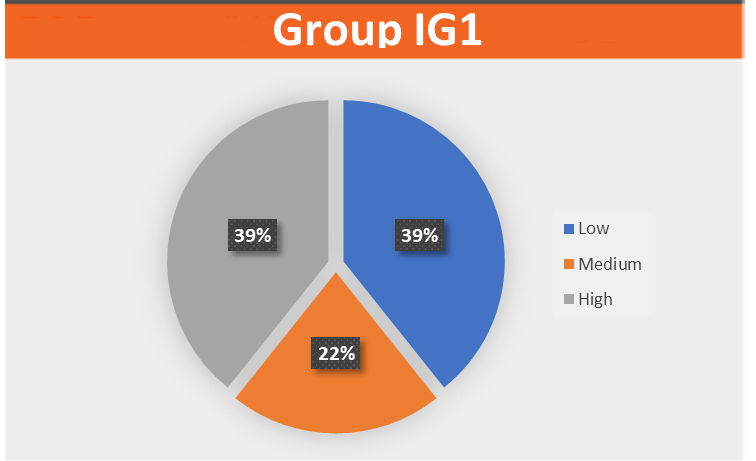
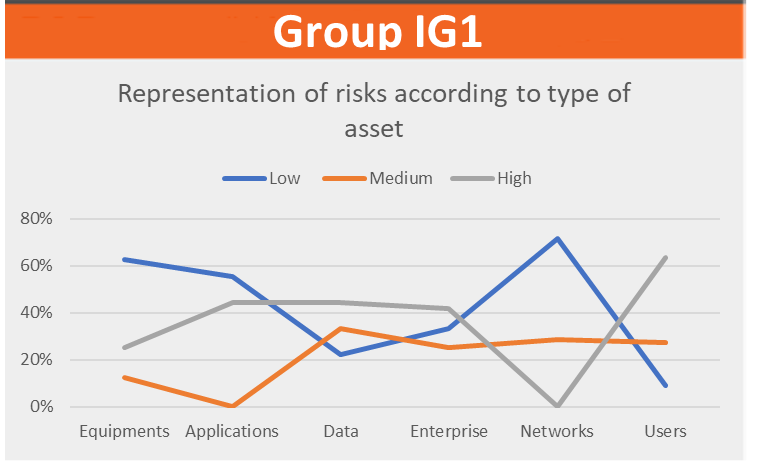
For a manager, a cybersecurity audit is a valuable tool to assess the effectiveness of the company’s cybersecurity measures. Audit results can help the executive and IT team identify areas for improvement and make informed decisions to better protect sensitive company information and assets from cyber threats. Additionally, auditing can help the executive ensure that the business is compliant with applicable regulations and standards, and mitigate the risk of data breaches and financial losses.
Like the financial audit, the external cybersecurity audit is an important tool to ensure the overall health and integrity of an organization. It helps protect the organization’s assets, reputation and compliance while enabling it to make more informed decisions.
Want to know more? Our articles on the subject might interest you:

